Introduction
Security today places us in a position where we create and maintain a long list of passwords. Fewer passwords to remember are better as it minimizes the risk of forgetting the important ones. The memory problem can be solved by using a sequence of letters or numbers that relate to something that is very familiar to us. Unfortunately this can mean that the PIN number for the security key pad at home or work ends up the same as the PIN number for our ATM card. Not an ideal situation. Alternatively they can be written down. If this method is chosen, try not to use the reverse side of ATM bank statements.
PIN numbers are relatively easier to remember and secure so long as you can avoid dates which have a personal meaning and are not common knowledge amongst your work colleagues and associates.
The focus for this article is to address passwords when interacting with the K2 Environment. This may be either the K2 Portal or a production K2.net environment.
Resolving K2 Portal Logins
If you are experiencing problems with logging into K2 Portal and you are sure that the username and password entered is correct, please contact portal@k2workflow.com. Please do not contact support@k2workflow.com.
Your account details can be emailed to you once you have been verified as the account holder.
General K2.net Production Environment Guidelines |
| 1. | Always use strong passwords. The difference between a strong password and a weak one is discussed further along in this article |
| 2. | If passwords must be written down on a piece of paper, store the paper in a secure place and destroy it when it is no longer needed. |
| 3. | Never share passwords with anyone. |
| 4. | Use different passwords for all user accounts (This may require developing a secure method of recording the passwords. |
| 5. | Change passwords immediately if they may have been compromised. |
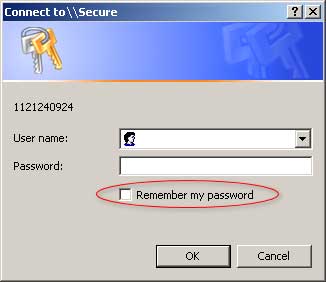
Caution is advised where passwords can be saved on computers. Some dialog boxes, such as those for remote access (see below) and other telephone connections have a check box which enables the dialog to remember your password. Although this seems like a good idea, selecting this option poses a potential security threat. This option shouldn’t be used unless the resource being logged into is not a security sensitive resource. |
| | 
|
| Best Practices |
| • | Passwords should be at least seven characters long |
| | Windows passwords can be up to 127 characters long. However, if you are on a network that also has computers running Windows 95 or Windows 98, consider using passwords that are not longer than 14 characters. Windows 95 and Windows 98 support passwords of up to 14 characters. If your password is longer, you might not be able to log on to your network from those computers. |
| • | The password should contain a combination of numeric, alphanumeric characters and symbols e.g. J*p2leO4>F |
| • | Ensure that the password fulfills the criteria for strong password, see the next section |
| • | Avoid passwords that contain commonly known personal information such as names of family members, friends and pets |
| • | Contain numbering that is incremental i.e. password 1, password 2, etc. |
| • | The password construct must be as random as possible. This does remove any inherent intuitiveness for remembering it but then does improve security |
| |
| Strong Vs Weak Passwords |
| A weak password: |
| • | Is no password at all. |
| • | Contains your user name, real name, or company name. |
| • | Contains a complete dictionary word. For example, Password is a weak password. |
| • | An example of a weak password is Hello2U! |
| |
| A strong password: |
| • | Is at least seven characters long. |
| • | Does not contain your user name, real name, or company name. |
| • | Does not contain a complete dictionary word. |
| • | Is significantly different from previous passwords. Passwords that increment (Password1, Password2, Password3 ...) are not strong. |
| • | Contains characters from each of the following four groups: |
| | - | English uppercase characters (A through Z) | | | - | English lowercase characters (a through z) | | | - | Base 10 digits (0 through 9) | | | - | Non-alphabetic characters (for example, !, $, #, %) |
|
| • | An example of a strong password is J*p2leO4>F. |



