How To: Configure PingIdentity to Log In to K2 Sites
KB002484
PRODUCTHow To: Configure Okta to Log In to K2 Sites
TAGS
Summary
This article provides details about the ability for K2 Cloud customers to use Microsoft Azure Active Directory (AAD) when AAD is federated to PingIdentity for authentication. In this scenario, identities must be stored in AAD for every user expected to use K2 Cloud sites and services, including K2 Management, K2 Designer, K2 Workspace, and K2 mobile apps.
Authentication Flow
Microsoft Azure AD (AAD) is the sole Identity Provider (IdP) within K2 Cloud and users are expected to be presented to K2 for authorization following an authentication pipeline by AAD. In some circumstances, you may want to delegate the final authentication of a user to a system outside of AAD, in this case, PingIdentity, to serve as the location where identity is validated. Users that are in an environment configured for this type of federated authentication use this authentication flow:
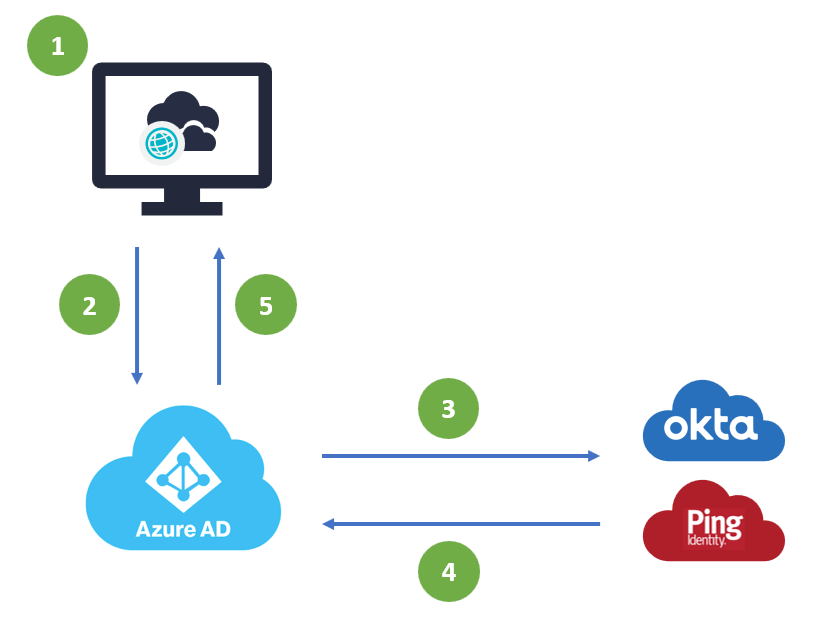
- A user accesses K2 Cloud and is prompted for authentication
- K2 Cloud redirects the user to AAD for authentication
- Once the user presents login details (username) they are directed to a federated Identity Provider for authentication
- Once the user is authenticated, the request is returned to AAD
- The authenticated user is matched to an AAD identity which is then passed to K2 Cloud for authorization
Steps
The scenario detailed in this article allows you to use PingIdentity authentication to log in to your K2 sites. The scenario assumes the following items are in place before starting:
- You have synchronized your on-premises Active Directory to Azure Active Directory (using Microsoft Azure Active Directory Connect)
- You have a Ping account
- You are an administrator for your PingIdentity and Azure Active Directory tenancies
- You are able to install PingFederate and set up a link between Azure Active Directory and Ping
- You have setup K2 for SharePoint to integrate with SharePoint Online (only required if you need K2 integration with SharePoint Online)
By configuring PingIdentity as a federated authentication provider, you can use Ping-based accounts, synchronized from Active Directory, to log in to K2 sites as well as SharePoint Online.
You may try to omit one or two pieces of this configuration, such as not having an on-prem Active Directory, but your results may vary. K2 has tested this configuration as described in this article but cannot support the configuration of PingFederate or variations of it.
If you have an environment or requirements that do not fit the scenario outlined in this article, create a Remote Services request to determine if K2 can help.
You can only use this approach if you have K2 for SharePoint Online and have synchronized your Active Directory to Azure Active Directory.
Step 1: Follow the Ping documentation to set up your authentication federation
- Use the following documentation from Ping to setup PingFederate with your Azure tenancy: PingFederate Integration with Azure Active Directory and Office 365
- Once you have configured PingFederate, you may need to wait for the synchronization to complete before you can log in.
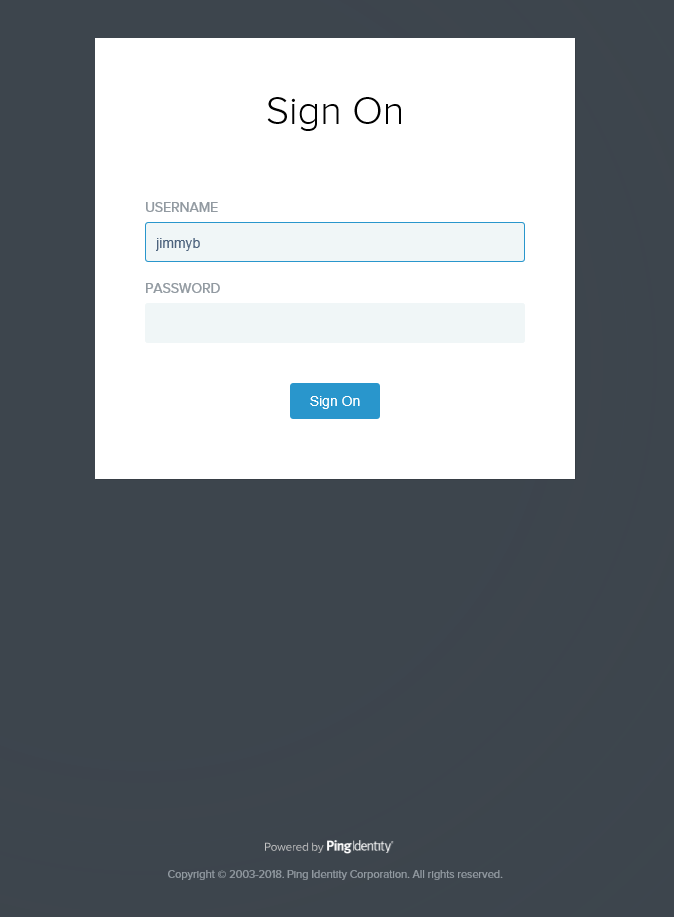
Step 2: Log In to a K2 Site using a Ping Account
You can log to one of your K2 sites using your Azure AD credentials via Ping.
- Select the AAD provider from the K2 login page
- Specify your username and password and click Sign On
- Your page opens and you can work with or design K2 objects.
Additional Resources
- Authentication and Authorization in K2
- PingFederate Integration with Azure Active Directory and Office 365
- Azure AD federation compatibility list (Microsoft)
- Federated identity (Wikipedia)


