Updating the K2 Service Account password in K2 after resetting in AD
kbt137088
PRODUCTObjective
After updating the K2 Service account due to an Active Directory Policy or alternative reason, the password needs to be updated within the K2 Product as well. K2 does not know the password has been changed in AD and has the old password cached.Before You Begin
Takes notes whether or not this account is used across multiple K2 Environments. If the same account is used elsewhere the same steps will most likely need to be done on other K2 environments as well.
Also, take note of any other applications outside of the K2 Product in which this could also be used to see if they have any caching mechanisms that might not update.
How-to Steps
The best starting point is to go through the K2 Blackpearl and K2 SmartForms Setup managers (Configure Option).
Find these in the Start Menu > K2 Blackpearl location. They can also be found within the install directory under Setup > K2 SmartForms Setup Folders.
When going through the Setup Managers you will be presented with the screen shown on the documentation link below:
K2 Blackpearl 4.7:
http://help.k2.com/onlinehelp/k2blackpearl/icg/4.7/default.htm#install/manual/farm_serviceaccconfig.htm
K2 Five:
http://help.k2.com/onlinehelp/k2five/icg/5.2/default.htm#install/manual/farm-serviceaccconfig.htm
Add the correct password and test to make sure it is valid.
After updating the Setup Manager they should now have correctly updated the Service Account Password across K2.
Most commonly, after the password is changed in AD but not in K2, the K2 Service account will get locked out within Active Directory. If this behavior appears within K2, double check the following locations to ensure that there are no other locations that are storing the old password as cached data:
1. The SSO credentials are stored if someone has specifically cached them within K2 Workspace. These credentials are encrypted and stored within the K2 DB under the [HostServer].[SecurityCredentialCache] table. Run the following update query to remove the old password from this table:
UPDATE [HostServer].[SecurityCredentialCache] SET Password = 0
WHERE UserName = 'DENALLIXK2Service'
Next, re-cache the credentials via the SSO cache page of Workspace. This will then store the correct new password that will need to be supplied.
2. Check the email connection strings that also use the K2 Service account. Verify that the password is correct by going to:
Check that all noted connection strings using the K2 Service account does have the proper password.
3. Control Panel > Credential Manager. Check if there are any Windows and/or Web Credentials stored on the machine for the relevant account.
4. If the account is running an App pool in IIS, it could have cached credentials.
Go into IIS > App Pools > right-click on App Pool > Advanced Settings > Process Model > Identity > click Ellipses next to username > click Set Button.
Re-add the correct credentials and then click Save. Do an IISreset to cement the change and then check that the browser loads properly.
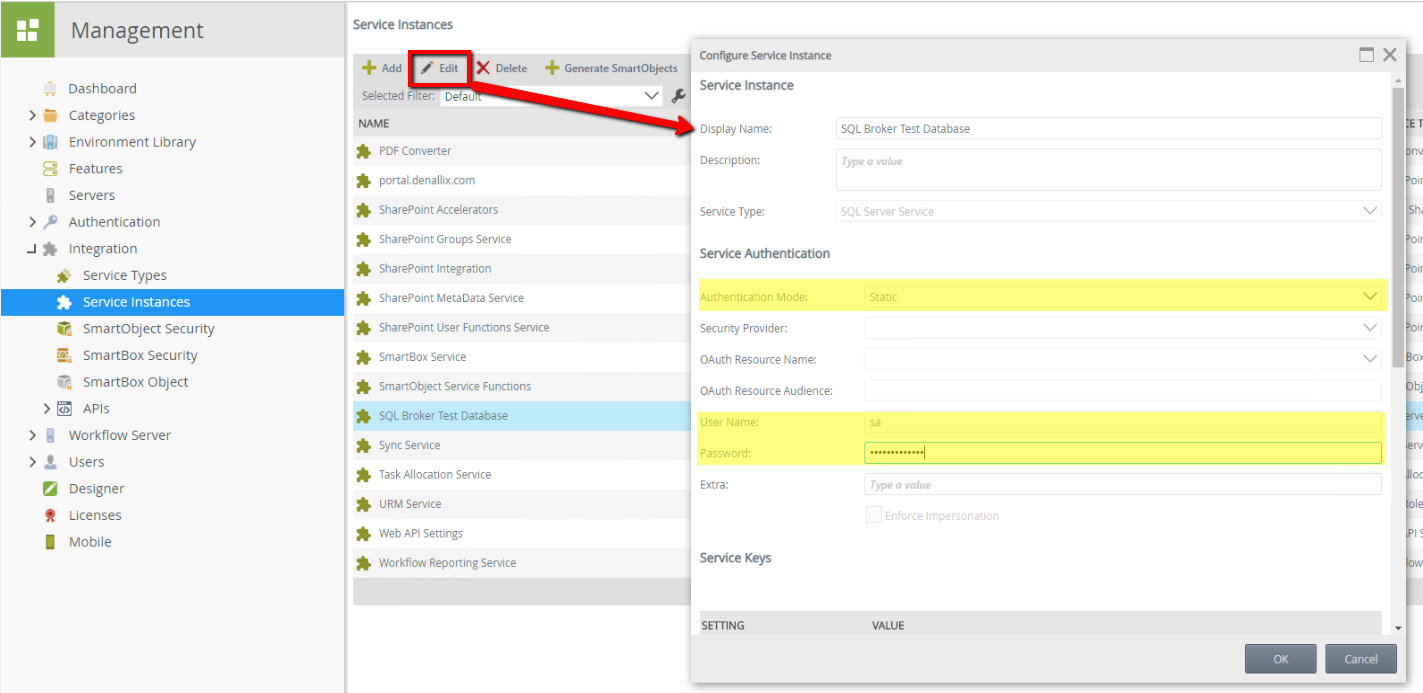
5. Check any Service Instances using Static Credentials for that Service account.
Edit the Service Instance and update the password manually by using the K2 Management site. You can edit the service instances on K2 Management underneath Integration > Service Instances, click on a service instance and then click the Edit button.
Once verified that the above settings are all set with the correct password, start searching outside of K2 for anything else that could be locking out this account within AD.
Additionally, check the Event Logs on the Domain Controller to figure out the exact location of where the account was hitting and getting locked out:
https://community.spiceworks.com/how_to/128213-identify-the-source-of-account-lockouts-in-active-directory


