When using APIs services with AAD authentication and clicking "Setup AAD Consent," returns HTTP 404 error
kbt141241
PRODUCTIssue
In K2 Five, when trying to use APIs services with AAD authentication and clicking on the "Setup AAD Consent" button, an error HTTP 404 is displayed.Symptoms
The error appears as:
"HTTP 404 error That’s odd... Microsoft Edge can’t find this page".
A link that looks like the example below is visible on the address bar:
https://login.microsoftonline.com/oauth2/authorize?client_id=239228c92-2222-22f2-b22e-fe2222ac222f&response_type=code&
redirect_uri=https://k2.denallix.com/Identity/Token/oauth/2/Authorized&resource=
https://graph.windows.net&prompt=admin_consent
Troubleshooting Steps
When looking at the URL that is opened when the consent button is clicked, you will notice that it is missing a GUID after the "https://login.microsoftonline.com/".
The correct URL should be, for example: "https://login.microsoftonline.com/333333f1-af343-4789-8ab56-333334ef92/oauth2/authorize".
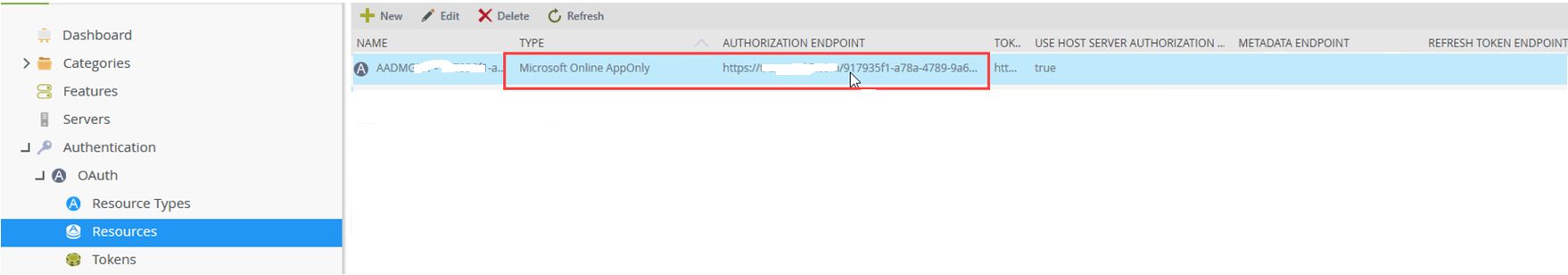
The "setup AAD Consent" button relies on the Authorization Endpoint of the OAuth resource of type "Microsoft Online AppOnly". This can be seen from Management Site > Authentication > OAuth > Resources.
To resolve this issue, please edit the resources to include the tenant ID.