How to configure REST Workflow API with Oauth Authentication on PostMan
kbt153745
PRODUCTObjective
How to correctly configure OAuth and K2 REST Workflow API CALLS for returning K2 Workflows with Bearer Token.Before You Begin
Note that this setup is possible for K2 5.1 and K2 Cloud and you will need access to the Azure Admin Portal.How-to Steps
Configuring Azure Active Directory
1. Create an App in Azure AD in the Azure Portal. In the left-hand navigation pane, click the Azure Active Directory service, click App registrations and click New application registration. (https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-v1-integrate-apps-with-azure-ad)
2. Rename it. In this example I've named it K2 Workflow:
3. Configure some properties and upload a logo (not essential)
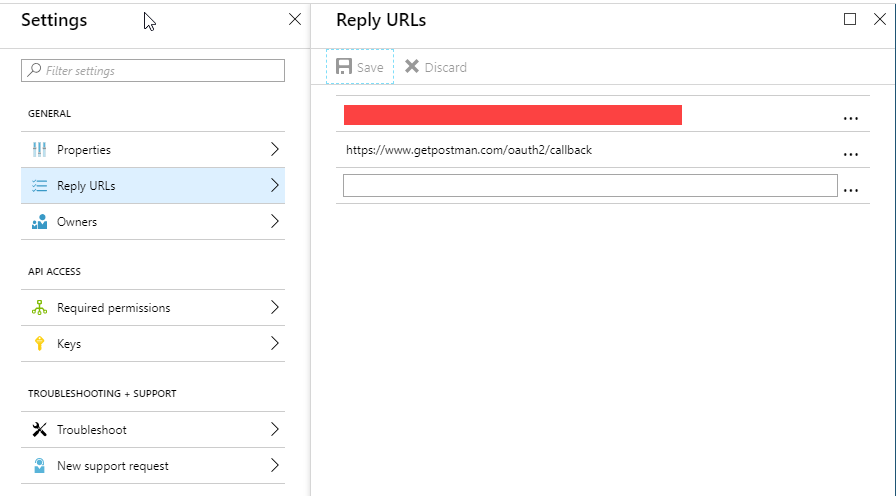
4. Next, add the reply URL of the target application. For postman this is: https://www.getpostman.com/oauth2/callback
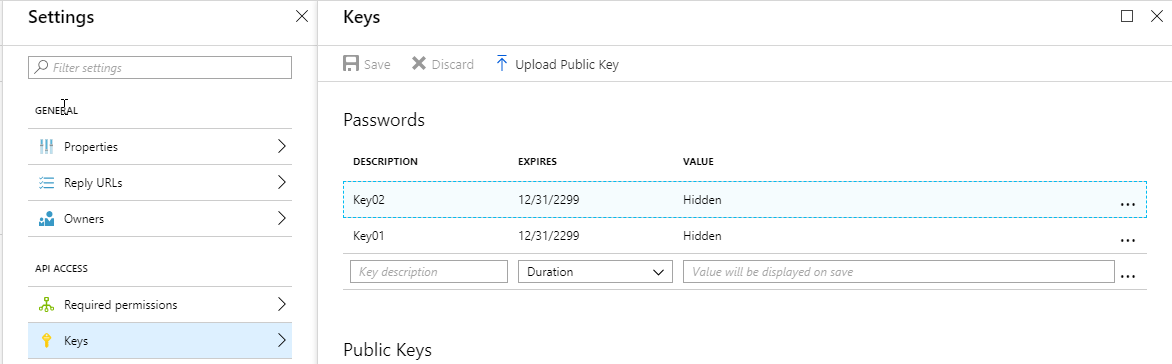
5. Also, a secret key is needed. This can be generated in the Keys section:
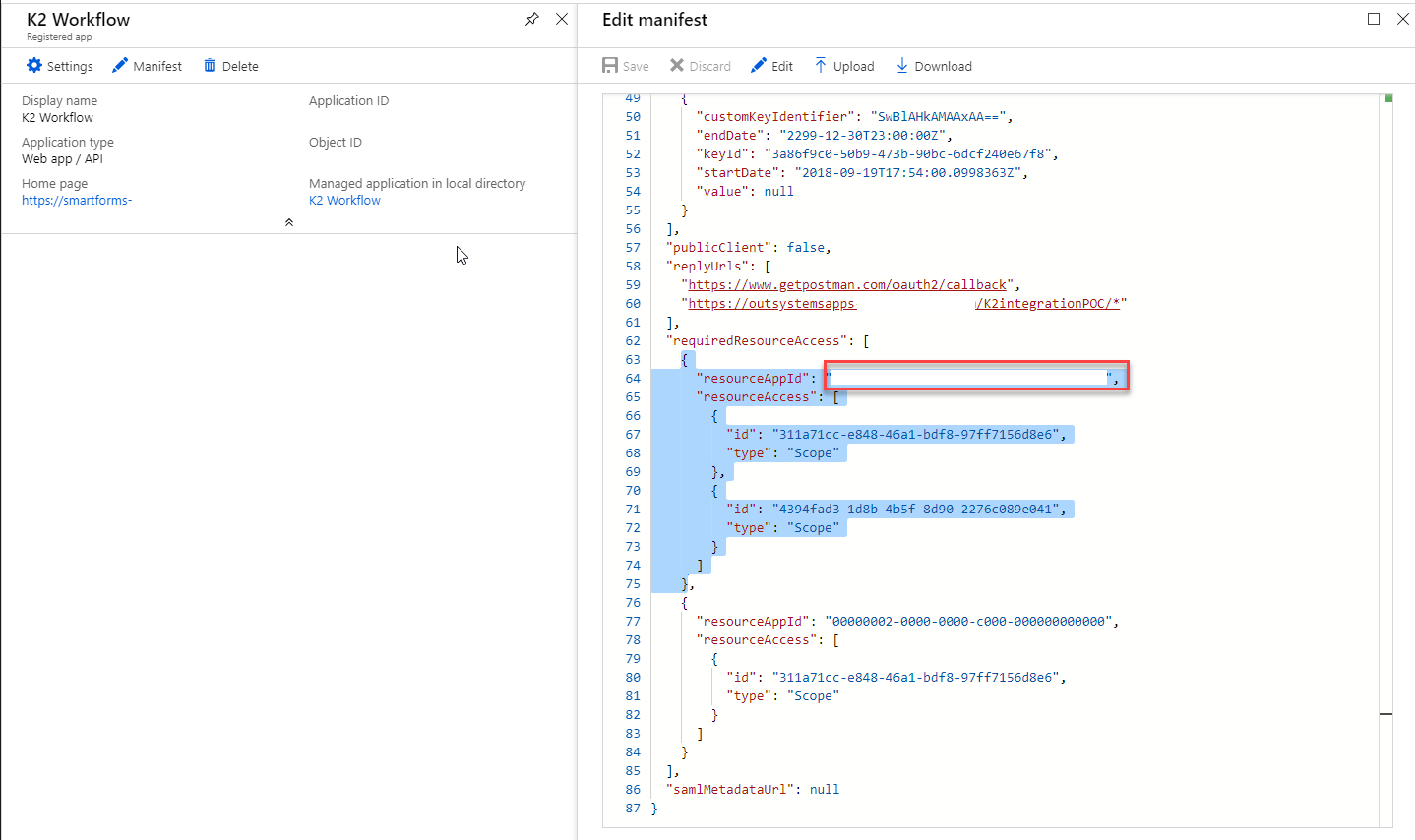
6. The last configuration is to add the ‘K2 API’ app (id: GUID) from the K2 tenant as a resource in the manifest code.
More info on the manifest can be found here: https://docs.microsoft.com/en-us/azure/active-directory/develop/reference-app-manifest
Configuring Postman
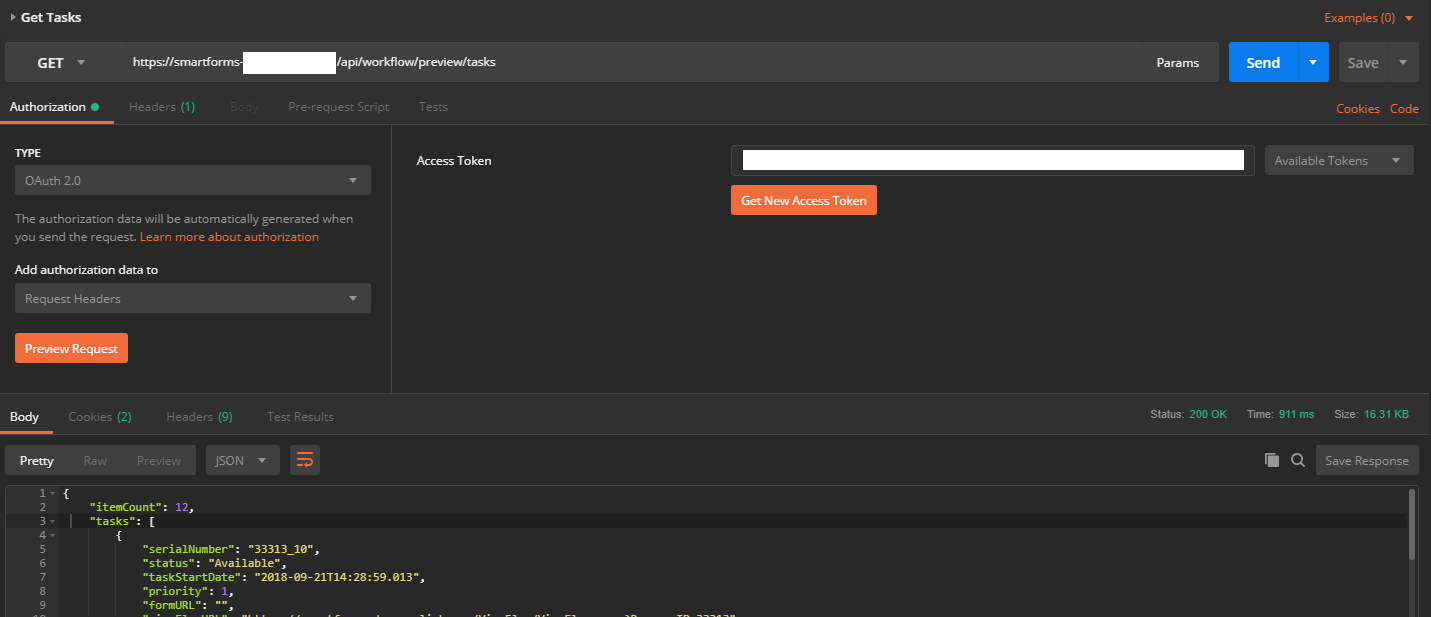
1. Add a new request to Postman and provide one of the API endpoints into the address bar (i.e. https://[environment]/api/workflow/[apiVersion]/tasks)
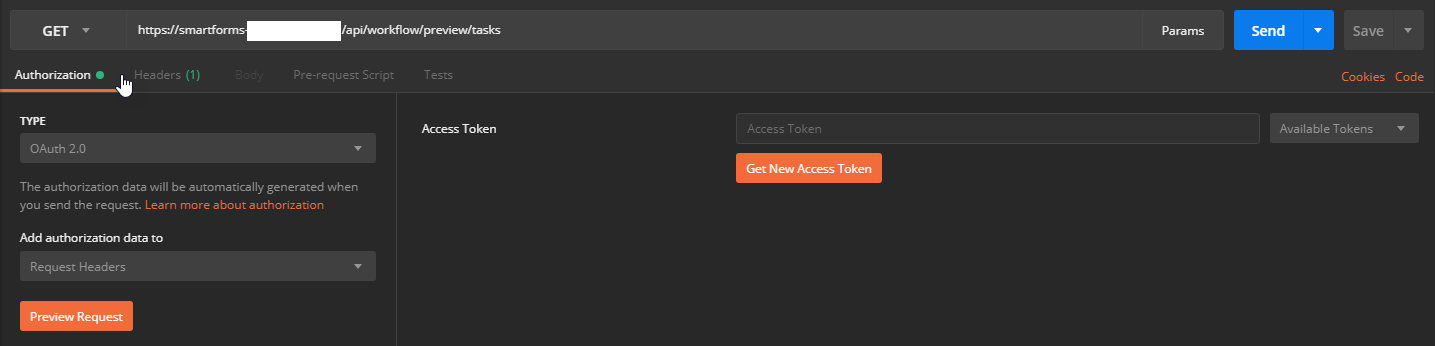
2. In the Authorization Tab, select OAuth 2.0 as Type. Then click the orange ‘Get New Access Token’ button.
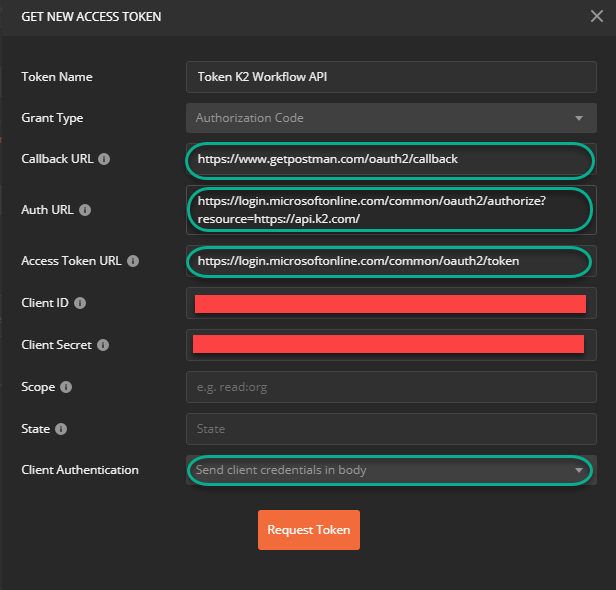
3. In the new window, provide the details shown in the screenshot. Use the App ID (from your recently made Azure App) as Client ID and use the Generated Key from your app as Client Secret. Also select ‘Send client credentials in body’ as Client Authentication. Be sure that the resource parameter ‘https://api.k2.com/’ is entered exactly as provided here:
4. Now select the ‘Request Token’ button and you will be redirected to a Microsoft login page. Log in with an AAD user which is also known in K2.
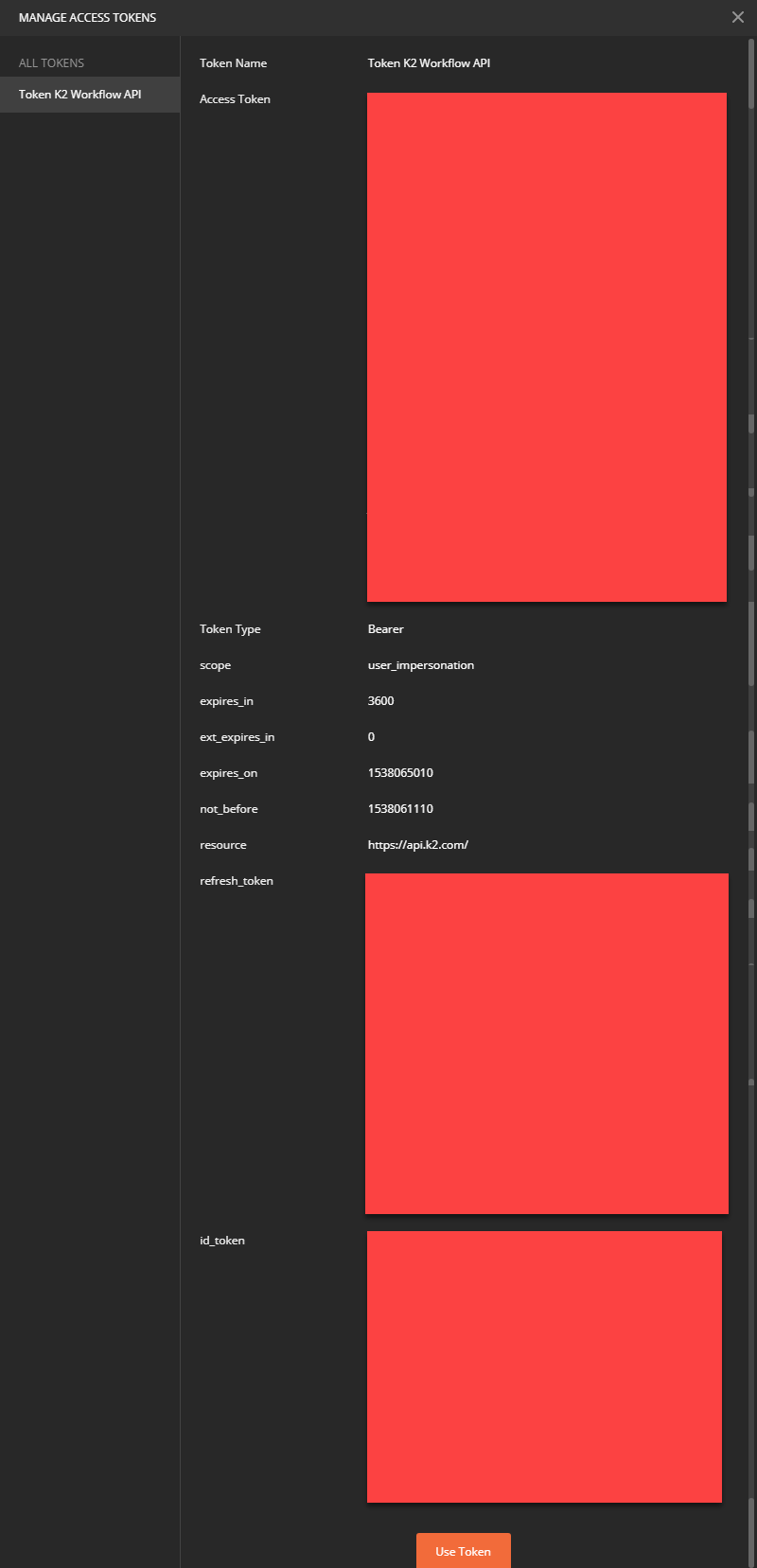
5. After a successful login, a new window in postman will show your token information, scroll down and select ‘Use Token.’
6. Now, you are ready to retrieve the task data using OAuth as authentication!